Here is a malicious e-mail that is trying to take advantage of the JAVA Security Bypass Zero-day exploit by impersonating popular professional networking website LinkedIn. The JAVA Security Bypass Zero-day exploit is a flaw that allows a malicious website, set up by a hacker, to infect your computer with malicious programs by just visiting the website.
This is how the malicious fake LinkedIn e-mail looks:
From: John Smith - LinkedIn (syllabifiesrev6077 @sprintrefugees.com)
Join my network on LinkedIn
LinkedIn
REMINDERS
Invitation reminders:
From John Smith (CEO at EZ Internet Solurions and Owner, EZ Internet Solurions)
PENDING MESSAGES
There are a total of 5 messages awaiting your response. Go to InBox now.
This message was sent to username@domain.com. Don't want to receive email notifications? Login to your LinkedIn account to Unsubscribe.
LinkedIn values your privacy. At no time has LinkedIn made your email address available to any other LinkedIn user without your permission. c 2013, LinkedIn Corporation.
The aim of this e-mail message is to, trick the victims into clicking on the links in it, which will take them to the malicious website: http://www.greetingsexperiencedone .asia/. A webpage on this website was created with a malicious Java Applet code to download malicious programs on to the victim's customer.
Please note that, you may receive other fake e-mails impersonating other legitimate websites and organizations.
If you receive the notification in your web browser below, prompting you to run the Java Add-On, please close that browser window.
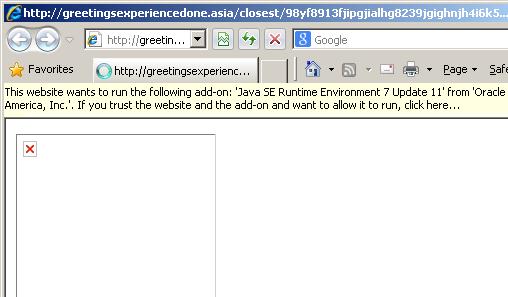
For information about the JAVA Security Bypass Zero-day exploit, click here.