Online users, do not open email attachments with file extensions or names ending with ".jar". This is because cybercriminals are sending out fake emails to potential victims with a malicious Java file (.jar) attached. The fake emails have a deceptive message, which instructs the recipients to open the same attached malicious Java file. But, any attempts to open the attached malicious ".jar" file will result in the recipients' computers getting infected with a virus, spyware, ransomware or other malware. Therefore, online users are asked not to open email attachments with names ending with ".jar", even if the email messages appear to have been sent from someone they know, or a legitimate organization
A Sample of an Email with a Malicious “.jar” File Attached
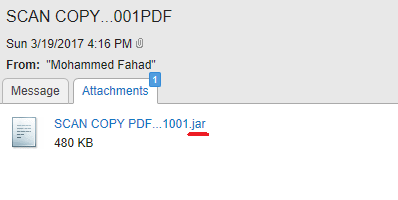
"SCAN COPY PDF...1001.jar"
The malicious attachment (.jar) contains a malware called “Backdoor:Java/Adwind” that installs a malicious component or codes onto your computer, which opens a backdoor on it. Once the backdoor is open on your computer, the cybercriminals behind the malicious email message will be able to access your computer silently, infect your computer with other malware, steal your information, and may use your computer to commit other cybercrimes that will be traced back to your computer. If this should happen to you, do not be surprised if one day you see the police at your doorsteps with a warrant to search your home and confiscate your computer, because some form of online criminal activities, which you know nothing about, were traced back to your location and computer.
Most antivirus software will detect and remove the malicious attachment before it infects your computer. But, the smart thing to do, is to delete the email message.
Online users who have received the fake email messages and have been tricked into opening the malicious “.jar” attachment are asked to do a full scan of their computers with their antivirus software.
Related article: